02 Mar Implementing Geo-Redundant DNS for Multi-Region Azure Architectures
Intro
Azure multi-region architectures promise high availability and low latency, but these benefits can be undermined if your Domain Name System (DNS) is not equally resilient.Today I’ll show you how to implement geo-redundant DNS in Azure to be sure that your applications remain reachable and performant across regions. What else? You will see the importance of geo-redundant DNS, the challenges of multi-region name resolution, an Azure-based solution approach and a practical implementation with PowerShell scripts. Finally, we’ll outline some other practices (like tuning DNS TTL and monitoring) to maximize reliability.
In a multi-region Azure deployment, DNS is important in directing traffic and service requests to the appropriate regional instance. Geo-redundant DNS means your DNS naming and lookup infrastructure is distributed across regions so that no single region failure or network latency issue can disrupt name resolution. This is importnat because even if you have workloads running in multiple Azure regions, a DNS outage or delay could make those workloads unreachable. For example, if all DNS queries must funnel through one region or one set of servers, a failure in that region can prevent users from resolving service endpoints, effectively causing an application outage despite other regions being healthy. Plus, DNS queries traveling across the globe to a single region introduce unnecessary latency for users or services in other regions. In short, without geo-redundant DNS, multi-region architecture may still have a single point of failure (or performance bottleneck) at the name resolution layer.
Azure’s own DNS services are built with global redundancy – Azure DNS (for public domains) offers a 100% availability SLA with a globally distributed name server infrastructure and Azure Private DNS zones are replicated across Azure’s infrastructure for resiliency. However, designing your DNS architecture properly is key to leveraging this. You need to ensure DNS zones and records are accessible in each region where your application runs and that clients (or VMs) in each region can quickly resolve DNS names without dependency on another region. We’ll see the specific challenges and how to address them using Azure Private DNS, Azure Public DNS and supporting services.
Challenges
Multi-region deployments face several DNS-related challenges if not architected for geo-redundancy. Common issues include:
DNS resolution delays
If DNS queries from one region must be resolved by a DNS server or service in a distant region, it adds network hops and latency. Applications might experience slower response times due to these DNS lookup delays, especially for services that do frequent name lookups. This is often seen when using a single centralized DNS server or an unlinked DNS zone for all regions.
Single-Region DNS failures
Relying on a DNS zone or server in only one region creates a single point of failure. If that region experiences an outage or network isolation, DNS names may fail to resolve (leading to NXDOMAIN or timeout errors) for the entire application. Even though your application has instances in other regions, they might become unreachable simply because the authoritative DNS cannot be contacted or is returning records pointing to the downed region.
Manual failover overhead
In some configurations, failing over an application to a secondary region requires manual DNS changes. For example, if your primary region’s IP addresses are hardcoded in DNS records, someone must update those records to point to the secondary region during an outage. This manual intervention can slow down recovery and is error-prone, potentially prolonging downtime.
Inconsistent DNS records across regions
If you maintain separate DNS zones per region (a strategy to improve local resiliency), keeping them synchronized is a challenge. A missing or outdated record in one region’s DNS can cause partial outages or connectivity issues. Without automation, administrators might have to update multiple zones every time a DNS record changes.
Latency and TTL mismatch
High DNS record Time-To-Live (TTL) values, while reducing DNS query traffic, can exacerbate latency during failovers. If a record is cached for too long on the client side, users might continue trying to reach a now-unavailable regional endpoint. Conversely, too low a TTL could increase the load on DNS infrastructure.
Solution
To achieve geo-redundant DNS in Azure, we need to distribute and duplicate DNS resolution across regions, leveraging Azure’s global DNS services. The solution approach involves using Azure Private DNS zones for internal name resolution and Azure Public DNS zones for external domains, in a way that eliminates single-region dependencies and minimizes lookup latency.
Azure Private DNS (for internal name resolution)
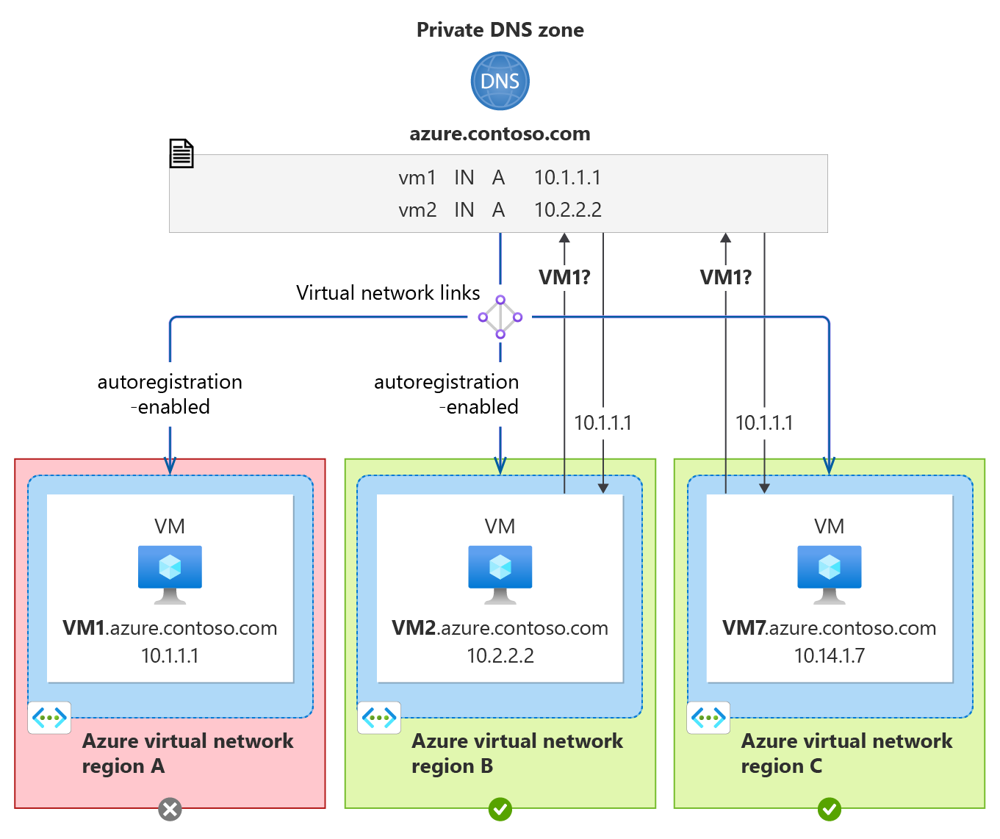
Azure Private DNS zones are global resources, meaning the DNS records in a private zone are automatically replicated across Azure’s infrastructure. By linking a private DNS zone to virtual networks in each of your regions, you ensure that VMs and services in those VNets can resolve DNS names locally without crossing region boundaries. For example, you might create a private zone like internal.contoso.local and link it to your East US and West Europe VNets. Azure’s platform will handle replicating all DNS records in that zone to the DNS servers in both regions. If one region experiences an outage, the other region’s DNS resolution is unaffected – resources in the secondary region can still query and get DNS responses because the zone data is globally available and up to date
Azure Public DNS (for external domains)
For publicly accessible endpoints (e.g., your website contoso.com), Azure DNS provides a globally distributed, highly available authoritative DNS service. A single Azure public DNS zone is served by name servers in multiple Azure regions worldwide, giving your users low-latency DNS responses from the nearest Azure location by default. Simply using Azure DNS for your domain inherently provides geo-redundancy, as Azure’s name servers are anycasted and redundant. To further enhance this for multi-region apps, you can use DNS-based traffic management. Azure Traffic Manager is a DNS load-balancer that can direct clients to different regional endpoints based on endpoint health or geographic proximity. By configuring Traffic Manager with profiles for your multi-region service (for example, an endpoint in East US and one in West Europe), the DNS system will hand out the IP of the healthiest or nearest region to the client. In a failover event, Traffic Manager detects the primary region is down and automatically starts returning the secondary region’s IP in DNS responses. All of this happens at the DNS layer, minimizing downtime.
Azure DNS Private Resolver
In cases where you have complex hybrid networks or need to improve DNS query performance further, Azure DNS Private Resolver can be introduced. The Private Resolver is an Azure service that you deploy in a region (or multiple regions) to act as a DNS server endpoint inside your VNet. It can forward queries between on-premises and Azure or between Azure VNets, according to rules you define. For geo-redundant DNS setups, you could deploy an instance of Azure DNS Private Resolver in each region, ensuring that even conditional DNS forwarding or hybrid name resolution has no single region dependency. For example, an on-premises DNS server could forward queries to an Azure Private Resolver in Region A, but if Region A is down, you might have a secondary forwarder in Region B. The configuration of Private Resolver is beyond our scope here, but it’s a powerful tool for distributed DNS resolution in advanced scenarios.
PowerShell
Automating DNS configuration across multiple regions for consistency and ease of management. Let’s start from PowerShell scripts and examples to set up geo-redundant DNS in Azure and keep it in sync. We’ll cover:
- Creating and Linking Azure Private DNS Zones across Regions – to ensure internal DNS names resolve in each region.
- Replicating and Updating DNS Records across multiple zones – so that changes in one region’s DNS are propagated to others.
- Monitoring and Verification – using scripts to check that DNS records are consistent and resolvable from each region.
Prerequisites
Ensure you have the Azure PowerShell Az module installed and you’re logged in (
Connect-AzAccount). Also, have the necessary permissions to create DNS zones and records in the target resource groups and to link virtual networks.
1. Setting up a Geo-Redundant Private DNS Zone
First, let’s create a private DNS zone and link it to virtual networks in two Azure regions (for example, East US and West Europe). This will allow VMs and services in both VNets to resolve DNS records from the same zone locally.
# Variables
$zoneName = "contoso.internal" # DNS zone name for internal use
$primaryRG = "Network-RG-EastUS" # Resource group for primary region resources
$secondaryRG = "Network-RG-WestEU" # Resource group for secondary region resources
$vnetName1 = "VNet-EastUS" # VNet in primary region (East US)
$vnetName2 = "VNet-WestEurope" # VNet in secondary region (West Europe)
# 1. Create the Private DNS zone (in primary region RG, though location is global)
New-AzPrivateDnsZone -Name $zoneName -ResourceGroupName $primaryRG
# 2. Retrieve the virtual network objects for both regions
$vnet1 = Get-AzVirtualNetwork -Name $vnetName1 -ResourceGroupName $primaryRG
$vnet2 = Get-AzVirtualNetwork -Name $vnetName2 -ResourceGroupName $secondaryRG
# 3. Link the DNS zone to both virtual networks (enable registration if VM DNS autoregistration is desired)
New-AzPrivateDnsVirtualNetworkLink -ZoneName $zoneName -ResourceGroupName $primaryRG `
-Name "Link-EastUS" -VirtualNetworkId $vnet1.Id -EnableRegistration:$true
New-AzPrivateDnsVirtualNetworkLink -ZoneName $zoneName -ResourceGroupName $primaryRG `
-Name "Link-WestEU" -VirtualNetworkId $vnet2.Id -EnableRegistration:$true
In the above script, we:
- Created a Private DNS zone named
contoso.internal. The zone is stored in an Azure resource group (East US in this case), but as noted earlier, private DNS zones are global and not tied to that region’s physical location. - Fetched the Azure VNet resources in East US and West Europe.
- Created Virtual Network Links for the zone to each VNet. This publishes the zone’s records to the DNS service in those VNets. We set
-EnableRegistration:$trueto turn on auto-registration of Azure VM hostnames in the zone for those VNets (optional). With links in place, any VM in those networks can resolve names incontoso.internalinternally, and if VMs are set to register, they’ll automatically add their A records to the zone.
At this point, the DNS zone contoso.internal is accessible in both regions. Azure will replicate all records in that zone globally, so queries in West Europe do not have to reach East US – they are answered locally. If East US were to go offline, West Europe VNet would still be able to resolve *.contoso.internal names from the zone without issue
2. Replicating DNS Records to a Secondary Zone (Optional for Region-Specific Zones)
If you choose to maintain separate DNS zones per region (for example, two zones both named contoso.internal in different resource groups or subscriptions), you’ll want to automatically replicate record changes from one zone to another. Below is a PowerShell snippet that copies records from a primary private DNS zone to a secondary one. This can be run whenever changes are made, or on a schedule, to keep zones in sync:
# Assume $zoneName, $primaryRG, and $secondaryRG are defined as before,
# and the primary zone already exists with records.
# Create the secondary DNS zone (if not already created)
$secondaryZone = Get-AzPrivateDnsZone -Name $zoneName -ResourceGroupName $secondaryRG -ErrorAction SilentlyContinue
if (-not $secondaryZone) {
$secondaryZone = New-AzPrivateDnsZone -Name $zoneName -ResourceGroupName $secondaryRG
}
# Fetch all record sets from the primary zone
$recordSets = Get-AzPrivateDnsRecordSet -ZoneName $zoneName -ResourceGroupName $primaryRG
# Loop through each record set and recreate it in the secondary zone
foreach ($record in $recordSets) {
if ($record.RecordType -in @("A","AAAA","CNAME","MX","TXT","SRV")) {
# Prepare parameters for the new record
$recordName = if ($record.Name -eq $zoneName) { "@" } else { $record.Name } # Use '@' for zone apex
$ttl = $record.TTL
# Build the record configuration(s) for private DNS
$recordConfigs = @()
foreach ($recVal in $record.Records) {
# Create corresponding record config based on type
switch ($record.RecordType) {
"A" { $recordConfigs += New-AzPrivateDnsRecordConfig -IPv4Address $recVal.IPv4Address }
"AAAA" { $recordConfigs += New-AzPrivateDnsRecordConfig -Ipv6Address $recVal.Ipv6Address }
"CNAME"{ $recordConfigs += New-AzPrivateDnsRecordConfig -Cname $recVal.Cname }
"MX" { $recordConfigs += New-AzPrivateDnsRecordConfig -Exchange $recVal.Exchange -Preference $recVal.Preference }
"TXT" { $recordConfigs += New-AzPrivateDnsRecordConfig -Value ($recVal.Value -join "") }
"SRV" { $recordConfigs += New-AzPrivateDnsRecordConfig -Priority $recVal.Priority -Weight $recVal.Weight `
-Port $recVal.Port -Target $recVal.Target }
}
}
# Create or update the record in the secondary zone
New-AzPrivateDnsRecordSet -ZoneName $zoneName -ResourceGroupName $secondaryRG `
-Name $recordName -RecordType $record.RecordType -TTL $ttl -PrivateDnsRecords $recordConfigs -Overwrite
}
}
This script does the following:
- Checks if the secondary zone exists and creates it if not.
- Retrieves all record sets from the primary zone.
- Iterates through each record set and, for the common record types (A, AAAA, CNAME, MX, TXT, SRV), reconstructs the record in the secondary zone. We skip NS and SOA records because those are created by Azure automatically for each zone and usually shouldn’t be manually duplicated.
- Uses
New-AzPrivateDnsRecordSet -Overwriteto add or update records in the secondary zone with the same names, values, and TTLs as the primary.
Note: The above is a basic replication approach. In a real-world implementation, you might want to refine this (e.g., remove records that were deleted in primary, handle PTR records if needed, etc.). You could also use Azure CLI (
az network private-dns zone export/import) to export zone files and import them to another zone as an alternative.
After running this, you would have two independent private DNS zones (one in each region’s resource group) with identical record sets. Workloads in each region would use their local zone for resolution. If one region’s zone or network is down, the other region’s zone is still fully functional with all necessary records. As mentioned, this setup particularly shines in active/active configurations – for example, two regions hosting the same service – because each region can have DNS records pointing to the local instance of the service. Clients automatically use the local DNS records, but if a failover occurs, clients in the failover region already have the needed DNS records to reach the service in that region
3. Updating Multiple DNS Zones in Automation
Instead of full export/import each time, you might maintain a script to update both primary and secondary zones whenever a DNS change is needed. For instance, if you add a new application server that needs an A record in your internal DNS, you can use a loop to add it to all relevant zones:
# Define the list of zones (could be private or public DNS zones) to update
$zonesToUpdate = @(
@{ Name = "contoso.internal"; RG = $primaryRG; IsPrivate = $true },
@{ Name = "contoso.internal"; RG = $secondaryRG; IsPrivate = $true }
)
$recordName = "appserver1" # the record we want to add
$recordIP = "10.10.5.4" # the IP address of the new server
$ttl = 300 # TTL of 5 minutes
foreach ($zone in $zonesToUpdate) {
if ($zone.IsPrivate) {
# Add A record to a Private DNS zone
New-AzPrivateDnsRecordSet -ZoneName $zone.Name -ResourceGroupName $zone.RG `
-Name $recordName -RecordType A -TTL $ttl `
-PrivateDnsRecords (New-AzPrivateDnsRecordConfig -IPv4Address $recordIP)
} else {
# Add A record to a Public DNS zone
New-AzDnsRecordSet -ZoneName $zone.Name -ResourceGroupName $zone.RG `
-Name $recordName -RecordType A -TTL $ttl -IPv4Address $recordIP
}
Write-Host "Added $recordName.$($zone.Name) to zone in RG $($zone.RG)"
}
This snippet can be integrated into deployment scripts or CI/CD pipelines, so whenever a new DNS entry is created or an existing one is changed, the script ensures all copies of the zone receive the update. In the above example, I demonstrate it for both private and public zones (New-AzDnsRecordSet is used for Azure Public DNS zones).
4. Monitoring and Verification
To confidently operate geo-redundant DNS, you should monitor that records are resolving correctly in all regions and that zones remain in sync. Azure Monitor can help by collecting metrics like DNS query volumes and resolution errors on Azure DNS zones. Additionally, you can use custom scripts to periodically verify DNS from different regions. For example, you might deploy a simple Azure Automation runbook or use Azure CLI in Cloud Shell targeting different regions to test name resolution:
# Pseudo-code for testing DNS resolution from two regions (requires context of running in those regions)
$testName = "appserver1.contoso.internal"
# In East US context:
$resultEast = Resolve-DnsName -Name $testName -Server 168.63.129.16
Write-Host "East US resolution for $testName -> $($resultEast.IPAddress)"
# In West Europe context:
$resultWE = Resolve-DnsName -Name $testName -Server 168.63.129.16
Write-Host "West Europe resolution for $testName -> $($resultWE.IPAddress)"
What we did? Azure VMs (and Cloud Shell sessions) use the default DNS server IP
168.63.129.16which is a regional Azure DNS resolver. The above commands, if run from VMs in each region, ask the local Azure DNS to resolve the name. You should see the appropriate IP answer (possibly the same IP if using one global zone or different regional IPs if using region-specific zones).
Another monitoring approach is to compare zone record sets directly via script. For instance, to ensure two Azure DNS zones are identical, you could retrieve records from both and do a comparison:
# Compare records between primary and secondary zone for consistency
$primaryRecords = Get-AzPrivateDnsRecordSet -ZoneName $zoneName -ResourceGroupName $primaryRG
$secondaryRecords = Get-AzPrivateDnsRecordSet -ZoneName $zoneName -ResourceGroupName $secondaryRG
# Simple comparison: check that the count and names of record sets match
if ($primaryRecords.Count -ne $secondaryRecords.Count) {
Write-Warning "Record count differs between primary and secondary zones!"
}
else {
foreach ($rec in $primaryRecords) {
$match = $secondaryRecords | Where-Object { $_.Name -eq $rec.Name -and $_.RecordType -eq $rec.RecordType }
if (-not $match) {
Write-Warning "$($rec.Name) [$($rec.RecordType)] is missing in secondary zone."
}
# (Further comparison of record values can be done here)
}
}
This can be extended to alert if any discrepancies are found. In production, you might schedule such a script to run daily and notify the ops team if a DNS record exists in one zone but not the other.
Lastly, enable Azure Monitor Diagnostic Settings for your DNS zones. For public DNS zones, you can enable DNS query logs and metrics to be sent to a Log Analytics workspace or Azure Monitor Logs. This will allow you to create alerts on metrics like high failure rates of DNS queries or unusual latency. For private DNS, Azure provides metrics like Query Volume per zone and can integrate with Azure Monitor (as of recent updates). If using Azure DNS Private Resolver, you can also get metrics on resolution success/failure. Setting up an Azure Monitor alert rule to detect when DNS queries consistently fail (or when a region’s query volume drops unexpectedly, indicating a possible outage) can provide early warning of DNS issues.
Through these scripts and monitoring steps, you achieve an automated, observable DNS setup that complements your multi-region deployment. Your DNS is now as highly available as the rest of your architecture, with automation handling the heavy lifting of keeping everything in sync.
Wrapping it all up
Geo-redundant DNS is a cornerstone of resilient multi-region architectures in Azure. By ensuring that DNS zones (both private and public) are distributed across regions, you eliminate single points of failure in name resolution and reduce latency for regional clients. In this post, we discussed how Azure Private DNS zones can be linked or replicated across regions to provide continuous internal name resolution even during a regional outage and how Azure Public DNS (with services like Traffic Manager) can direct users to the healthiest region automatically. I provided PowerShell examples to automate the creation, synchronization and monitoring of DNS zones – practical steps that you can adapt in your environment to avoid manual configuration drift and expedite failovers.

No Comments